Subscribe to wiki
Share wiki
Bookmark
ZKM
The Agent Tokenization Platform (ATP):Build autonomous agents with the Agent Development Kit (ADK)
0%
ZKM
ZKM, or Zero-Knowledge MIPS, is an advanced architecture that combines MIPS (Microprocessor without Interlocked Pipeline Stages), a type of Reduced Instruction Set Computer (RISC) CPU architecture, with zero-knowledge proofs (ZKPs) to meet its goals of addressing fragmentation in the blockchain space by enhancing interoperability and unifying decentralized systems. [1][2]
Overview
ZKM is an open-source project utilizing the MIPS instruction set. It is focused on research-driven methods to improve verifiable computing for a more integrated blockchain experience. The project seeks to address fragmentation in the blockchain space by enhancing interoperability and unifying decentralized systems. ZKM is developing a general-purpose zkVM designed to integrate with various blockchain infrastructures and, eventually, non-blockchain systems. This integration aims to enable secure and decentralized communication of state changes between chains, which is critical for the broader adoption of blockchain technology. [1][3]
The project aims to overcome several challenges: removing the 7-day Withdrawal Window, achieving Unified Security for all Layer 2 (L2) solutions and alternative Layer 1 (Alt L1) blockchain networks, and enabling tamper-proof Internet of Things (IoT) and cloud computing. The goal is to facilitate faster and more convenient fund withdrawals, create a standardized security framework across various L2 and Alt L1 platforms, and improve the security and integrity of IoT devices and cloud computing systems. [1][3]
Architecture
zkVM
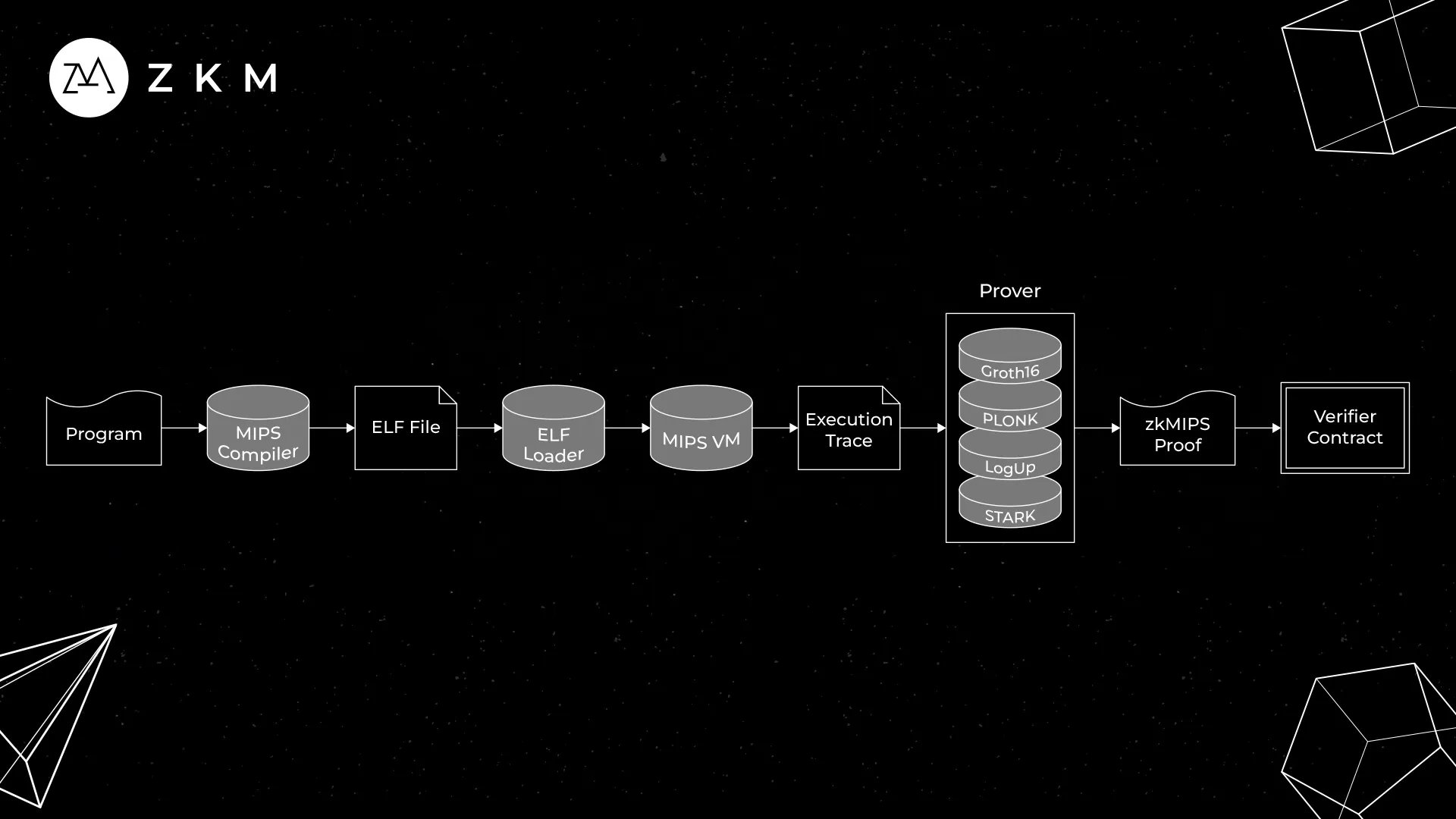
ZKM is developing the Zero-Knowledge Virtual Machine (zkVM), designed to facilitate zero-knowledge proofs across different computational tasks to enable verifiable computation for interoperability between blockchains, IoT devices, and other Web2 solutions. This involves integrating Zero-Knowledge technology with the MIPS architecture to create a verifiable computing system that ensures trust in computation results from untrusted computers. The generated Zero-Knowledge Proofs (ZKPs) may be stored on Ethereum, aligning with ZKM’s vision of using Ethereum as a foundational settlement layer for blockchain and non-blockchain technologies utilizing the zkVM. [4][5]
It executes computations and generates a ZKP to verify their validity and results. Unlike zkEVM, zkVM integrates with many computations, allowing developers to create and execute zero-knowledge applications regardless of the blockchain network. This versatility extends its use beyond financial and privacy-focused applications to areas like supply chain management, healthcare, and entertainment, where data integrity is crucial. [4][5]
ZK-MIPS
MIPS (Microprocessor without Interlocked Pipeline Stages) is a microprocessor architecture designed for simplicity, with a minimal set of instructions that allows for easier refinement. ZK-MIPS combines MIPS with ZK (Zero-Knowledge) technology. Due to MIPS's minimalistic nature, converting MIPS code into ZK-MIPS is relatively straightforward, resulting in fewer bugs and issues. This converted code is placed inside a specialized Virtual Machine (VM) that uses ZK architecture, creating what is known as ZK-MIPS. [3][6][7]
Zero-Knowledge (ZK) verifies computations or information without revealing the underlying data. In ZK-MIPS, this means proving that a computation was performed correctly inside the VM while potentially hiding the inputs. The computation is transformed into a different format suitable for processing with ZK using mathematical polynomials and various types of commitments. [3][6][7]
Features
ZK-MIPS provides universal ZKP security by securing the CPU/MIPS beneath all software layers, allowing users to benefit from ZKP security without needing to perform proofing themselves. ZKM is compatible with various virtual machines (VMs), such as MoveVM, WASM, and RustVM, and integrates seamlessly with different blockchain smart contract engines. Developers can adopt ZKM without altering their codebase, enjoying zero
- or low-cost integration and support for multiple smart contracts and programming languages. ZKM’s stable MIPS instruction set offers a consistent development environment, avoiding the instability of frequently changing EVM instruction sets. [7]
It leverages Ethereum's decentralized security base to validate transactions, ensuring robust security for blockchain and non-blockchain applications. The ZKM-enabled Hybrid Rollup enhances the user experience by providing instant confirmation and finality without the 7-day withdrawal wait, improving security through ZKP verification, and an extended fraud-proof challenge window for safe large transfers. ZKM also extends beyond Layer 2 solutions and blockchain, offering benefits to alternative Layer 1 blockchains, enabling tamper-proof IoT devices and enhancing security for cloud computing environments. [7]
Quantum Entangled Network
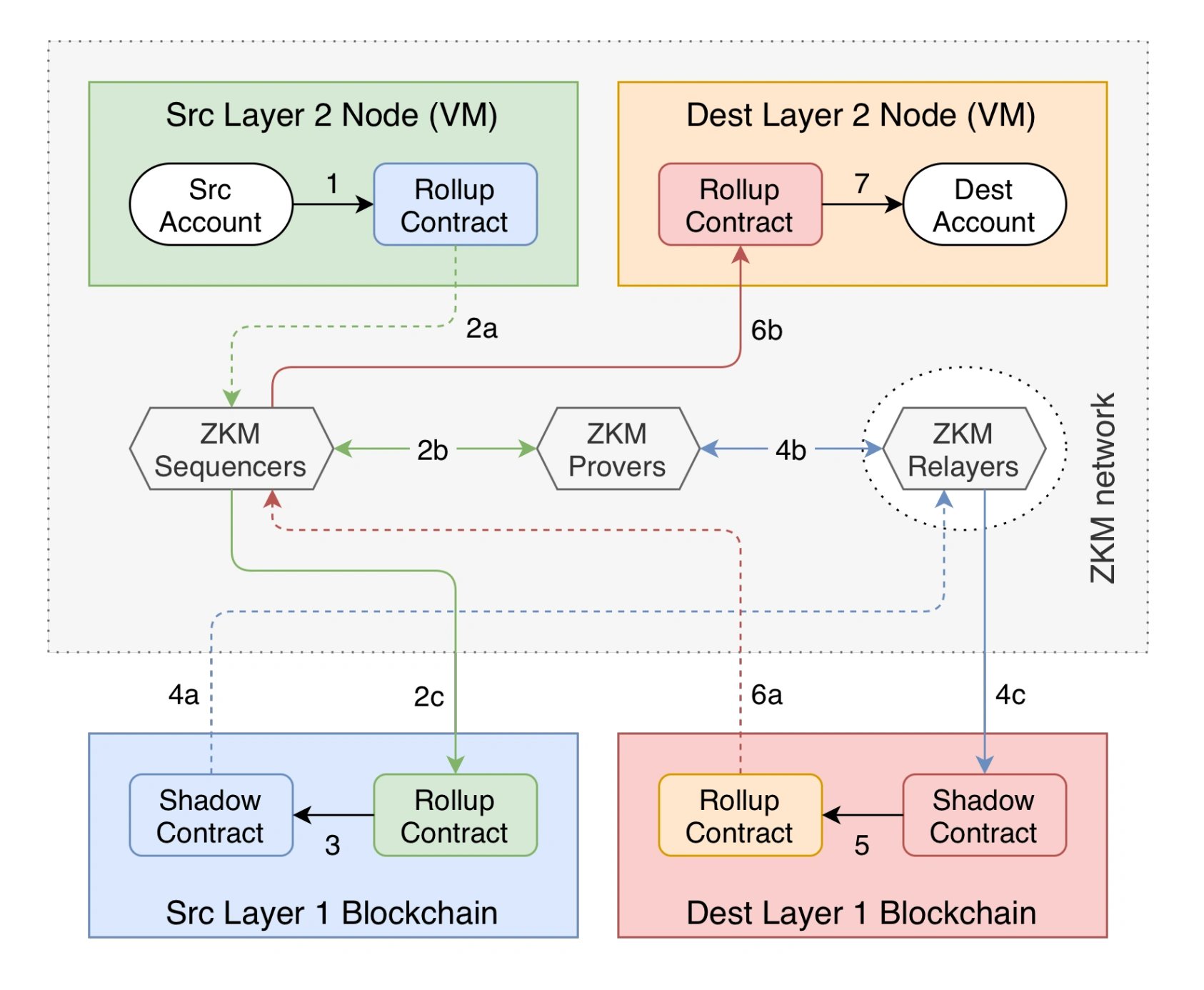
ZKM is developing the Quantum Network with Entangled Rollups to enable Universal Settlement. In this network, a "particle" represents a message, its "characteristics" are properties, and its "space" is blockchains. It ensures that a message on one blockchain is directly and immediately correlated with equivalent properties on other blockchains. Zero Knowledge Proofs (ZKP) are used to verify computation—retrieving data from a source chain and posting a ZKP to a destination chain—ensuring correct transaction execution and settlement. This method allows messages to correlate properties across previously incompatible blockchains within the Quantum Network. [8]
Universal Settlement
Universal Settlement refers to the ability for computations executed on one blockchain to have their results used on any other blockchain. Achieving this in a fully decentralized manner has been challenging. Current solutions often involve creating an intermediary blockchain between the source and destination chains to facilitate Universal Settlement, typically for token transfers. However, this approach reduces security, as there is no way to ensure that the intermediary system is decentralized enough to guarantee the secure transfer of assets. [8]
Entangled Rollups
The Entangled Rollup structure enables trustless communication between two rollups, allowing transactions to be executed, proved, and executed again on a destination Layer 2 (L2) while utilizing the security and cost-effectiveness of a Rollup. This structure facilitates interaction between incompatible blockchains through Layer 2s, supporting additional use cases and optimizations such as the Universal L2 Extension. The Universal L2 addresses fragmented liquidity across ecosystems by allowing users to burn and mint native assets to any Layer 2 that implements this structure, using a proof-of-burn mechanism and the Rollup's native mint function. [8][9]
Ecosystem
Contributor Points System
The Contributor POINTS System enables active participation in the ZKM ecosystem by earning points through various bounties and tasks. These non-transferable points track contributions on-chain, providing a way to quantify and recognize achievements within the ZKM community, including general promotion, protocol development, and educational advancements. Earning POINTS involves selecting a campaign from ZKM’s Contributor Board that matches one’s interests. Each campaign features a range of bounties covering various tasks and contributions. Completing these bounties results in accumulating POINTS. Accumulating more POINTS leads to unlocking exclusive rewards within the ZKM ecosystem. [10]
ZKM will offer various rewards for contributors, with additional opportunities to be added over time. Reward redemptions will begin four weeks after the initial launch of the Contributor Board and POINTS System. Available rewards will include early access to community initiatives, exclusive event invitations, level-based badges, project introductions, course completion certificates, and branded merchandise, among other items. [10]
ZKM Education Hub
The Education Hub is designed to guide users through the ZK (Zero-Knowledge) space, catering to beginners and experienced developers. Curated by Jeroen van de Graaf, Ph.D., a Senior Cryptographer at ZKM and Assistant Professor at the Federal University of Minas Gerais, the hub offers courses to advance education in ZK technology. Users can receive personalized support from the ZKM team and collaborate with other community members. [11][12]
The Education Hub provides curated content, including courses, video lectures, presentations, programming assignments, tutorials, and workshops. It also offers active community support, opportunities for direct interaction with the ZKM team through community calls and AMAs, and access to a content library with recommended resources to aid in ZK learning. [11][12]
Participants can earn ZKM POINTS by completing assignments and creating content which can be accumulated through various activities: [11][12]
- Watching video lectures and completing related mini-quizzes
- Completing programming assignments with GitHub links shared on Discord
- Writing blog articles or tweets expanding on concepts from “A High-Level Introduction To Zero Knowledge And SNARKS” or the ZKM Content Library
- Engaging in discussions on Discord
- Participating in community calls and AMAs
- Actively contributing to the Education Hub Discord channels
- Submitting contributions through the Contributor Board
Accumulating more points can unlock rewards such as early access to community initiatives, exclusive event invitations, and level-based badges. [11][12]
Proving Service
Proving Service offers developers access to high-performance servers designed to handle the computational demands of generating zero-knowledge proofs, specifically optimized for zk-MIPS, ZKM’s specialized zkVM software for integrating ZKP capabilities into various applications. Zk-MIPS supports Golang, allowing proof generation within existing Golang environments without complex modifications. Developers can compile Golang code into MIPS instructions using the standard Golang compiler and verify execution with ZKM’s proof service. Support for additional high-level languages will be introduced later. [13]
Delphi
Delphi, developed by Jeroen van de Graaf and Arjen K. Lenstra, is an advanced research initiative to share assessments of cryptographic assumptions. Most practical cryptographic protocols rely on computational or ad hoc assumptions, and evaluating these assumptions is crucial for understanding system risks. Discussions on these assumptions are often limited to informal settings or small groups. Delphi seeks to make these discussions explicit and public by collecting and sharing researchers' opinions on the strengths of key assumptions through an online questionnaire. [14]
The current Delphi paper focuses on classical cryptographic assumptions, while Delphi 2, a separate questionnaire, is being developed to address Ethereum, zkSNARKs, zk-friendly hash functions, and similar primitives. This effort aims to provide valuable comparisons of these newer primitives for the community. [14]

GOAT Network
On July 8th, 2024, ZKM co-founder Kevin Liu revealed a Bitcoin Layer 2 solution called GOAT Network, which is planned for a Q3 launch. The project aims to make GOAT Network the first decentralized Bitcoin Layer 2 with shared network ownership, introducing a decentralized sequencer model where node operators secure the network and earn yields on their Bitcoin, as well as fees from block production, transaction ordering, and maximal extractable value (MEV) opportunities. [16]
GOAT Network will use ZKM’s proving service for its ZK prover component. The progress of this service will influence the decentralization of the Proof Network. In Layer 2 rollup networks, a sequencer orders and batches off-chain transactions before submitting them to the main blockchain, while a prover generates cryptographic proofs to validate transactions, avoiding processing on the main chain. These roles currently represent single points of failure and potential censorship risks. Unlike Bitcoin's existing state channel Layer 2 solution, the Lightning Network, the GOAT Network is Ethereum Virtual Machine-compatible and supports smart contract functionality. [16]
“GOAT Network’s launch of a ) ) is a powerful first step in ZKM’s quest to unite the fragmented ) universe. We believe strongly in decentralization, and we’re excited to enable a shared-ownership model from day one.” - Kevin Liu, ZKM CEO and Co-founder.
Team
- Kevin Liu: CEO
- Jeroen Van De Graaf: Researcher
- Ming Guo: Chief Scientist
- Elena Sinelnikova: People & Team Culture Lead
- Lucas Peixoto Fraga: Researcher
- Pavel Sinelnikov: Dev Rel Lead
- Alice Liu: Education Lead
- Ben Wynn: Community Lead
- Berry Huang: Developer
- Angell Li: Developer
Partnerships
Investors
On May 7th, 2024, ZKM announced a successful Pre-A funding round in November 2023. The project raised $5M in a round led by OKX Ventures and joined by backers including Amber Group, P2 Ventures, Crypto.com, Leland Ventures, Pacific WaterDrip Digital Asset Fund, JSquare, Contribution Capital, and Metis Foundation. [15]
See something wrong?
The Agent Tokenization Platform (ATP):Build autonomous agents with the Agent Development Kit (ADK)
